Can a Nfs Secuirty Be Used Over Again
This browser is no longer supported.
Upgrade to Microsoft Edge to accept reward of the latest features, security updates, and technical support.
This article lists some mutual problems and known issues related to Azure NFS file shares. It provides potential causes and workarounds when these problems are encountered.
Applies to
| File share type | SMB | NFS |
|---|---|---|
| Standard file shares (GPv2), LRS/ZRS | | |
| Standard file shares (GPv2), GRS/GZRS | | |
| Premium file shares (FileStorage), LRS/ZRS | | |
chgrp "filename" failed: Invalid argument (22)
Crusade 1: idmapping is non disabled
Azure Files disallows alphanumeric UID/GID. So idmapping must be disabled.
Cause two: idmapping was disabled, but got re-enabled after encountering bad file/dir name
Fifty-fifty if idmapping has been correctly disabled, the settings for disabling idmapping gets overridden in some cases. For instance, when the Azure Files encounters a bad file name, it sends back an mistake. Upon seeing this particular mistake code, NFS v 4.1 Linux client decides to re-enable idmapping and the future requests are sent again with alphanumeric UID/GID. For a listing of unsupported characters on Azure Files, see this commodity. Colon is i of the unsupported characters.
Workaround
Check that idmapping is disabled and aught is re-enabling it, so perform the post-obit steps:
- Unmount the share
- Disable idmapping with # echo Y > /sys/module/nfs/parameters/nfs4_disable_idmapping
- Mount the share back
- If running rsync, run rsync with the "—numeric-ids" argument from a directory that does not take a bad dir/file name.
Cause 1: Unsupported storage account settings
NFS is only available on storage accounts with the following configuration:
- Tier - Premium
- Account Kind - FileStorage
- Regions - List of supported regions
Solution
Follow the instructions in our article: How to create an NFS share.
Cause 1: Request originates from a client in an untrusted network/untrusted IP
Unlike SMB, NFS does not have user-based authentication. The authentication for a share is based on your network security rule configuration. Due to this, to ensure only secure connections are established to your NFS share, y'all must use either the service endpoint or individual endpoints. To access shares from on-premises in improver to private endpoints, y'all must set up VPN or ExpressRoute. IPs added to the storage account's allowlist for the firewall are ignored. You must use one of the following methods to gear up admission to an NFS share:
- Service endpoint
- Accessed past the public endpoint
- Only available in the same region.
- VNet peering won't requite access to your share.
- Each virtual network or subnet must be individually added to the allowlist.
- For on-bounds admission, service endpoints can be used with ExpressRoute, point-to-site, and site-to-site VPNs only, nosotros recommend using private endpoint since it is more secure.
The following diagram depicts connectivity using public endpoints.
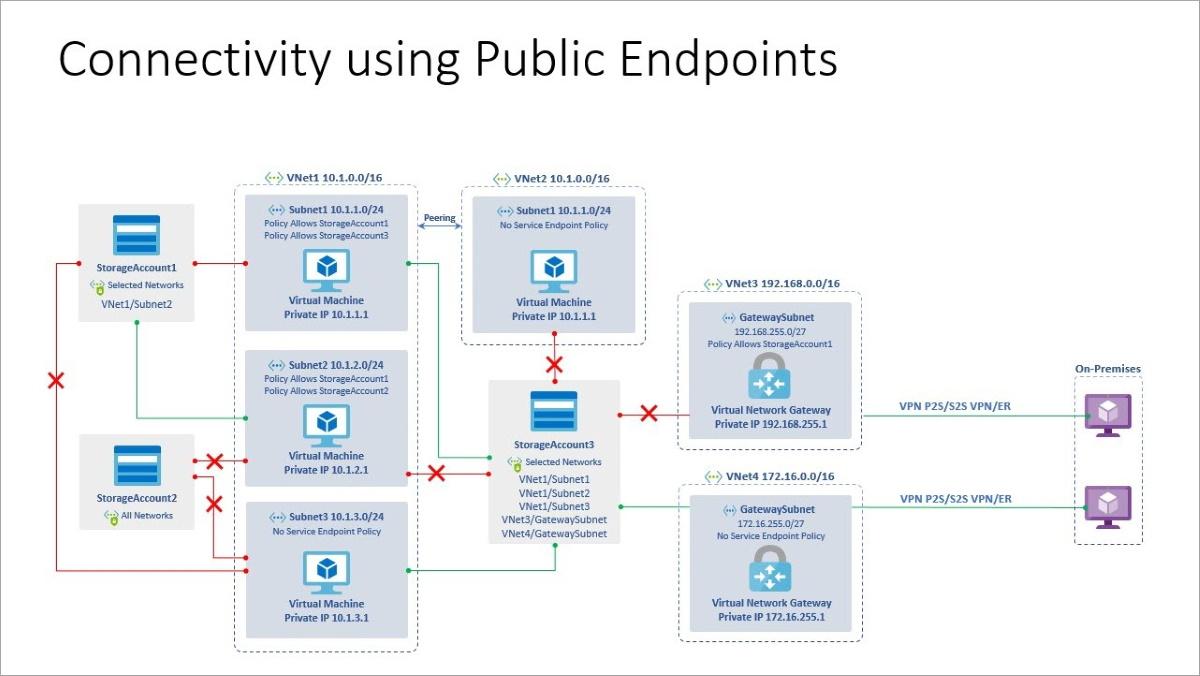
- Private endpoint
- Access is more secure than the service endpoint.
- Access to NFS share via private link is available from within and outside the storage account'south Azure region (cross-region, on-premise)
- Virtual network peering with virtual networks hosted in the private endpoint requite NFS share access to the clients in peered virtual networks.
- Private endpoints can be used with ExpressRoute, point-to-site, and site-to-site VPNs.

Cause 2: Secure transfer required is enabled
Double encryption isn't supported for NFS shares notwithstanding. Azure provides a layer of encryption for all data in transit between Azure datacenters using MACSec. NFS shares tin can but be accessed from trusted virtual networks and over VPN tunnels. No additional transport layer encryption is available on NFS shares.
Solution
Disable secure transfer required in your storage business relationship'southward configuration blade.
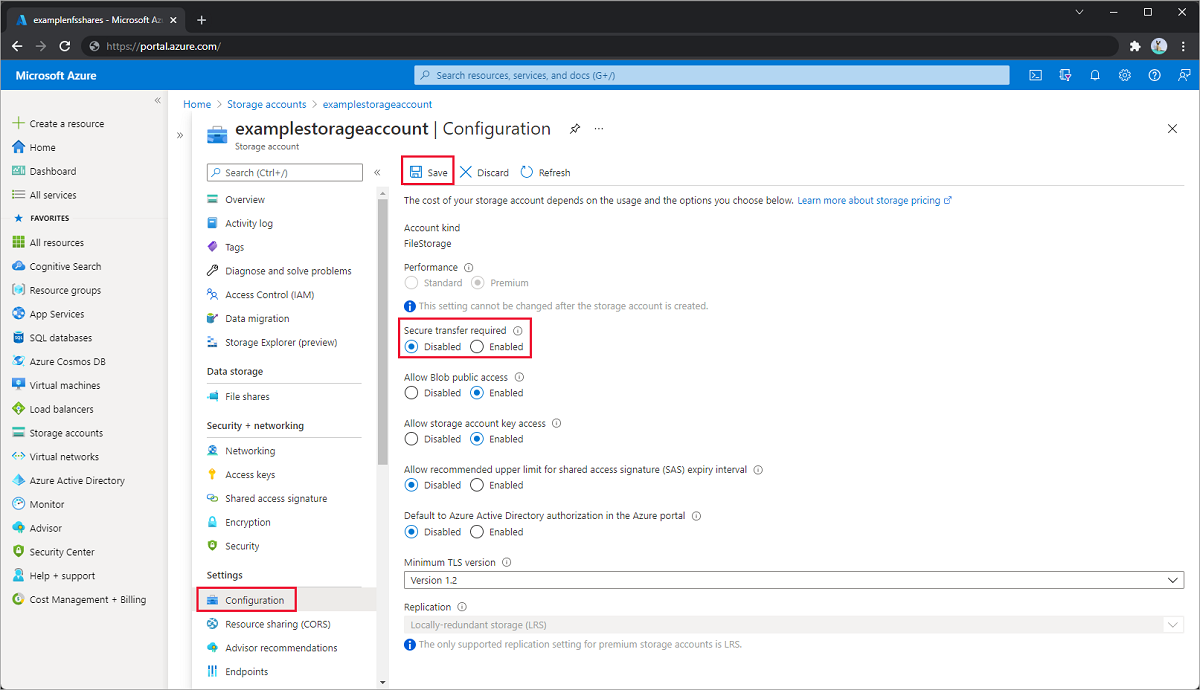
Cause iii: nfs-common packet is not installed
Before running the mount control, install the bundle by running the distro-specific command from beneath.
To cheque if the NFS bundle is installed, run: rpm qa | grep nfs-utils
Solution
If the package isn't installed, install the parcel on your distribution.
Ubuntu or Debian
sudo apt update sudo apt install nfs-common Fedora, Ruddy Lid Enterprise Linux viii+, CentOS viii+
Use the dnf packet manager:sudo dnf install nfs-utils.
Older versions of Red Hat Enterprise Linux and CentOS use the yum package manager: sudo yum install nfs-mutual.
openSUSE
Utilise the zypper package manager: sudo zypper install-nfscommon.
Crusade four: Firewall blocking port 2049
The NFS protocol communicates to its server over port 2049, brand sure that this port is open to the storage account (the NFS server).
Solution
Verify that port 2049 is open on your client by running the following command: telnet <storageaccountnamehere>.file.core.windows.net 2049. If the port isn't open, open it.
ls hangs for large directory enumeration on some kernels
Cause: A issues was introduced in Linux kernel v5.xi and was fixed in v5.12.5.
Some kernel versions take a issues that causes directory listings to upshot in an endless READDIR sequence. Very small-scale directories where all entries tin can be shipped in ane call won't have the problem. The problems was introduced in Linux kernel v5.eleven and was stock-still in v5.12.5. Then annihilation in between has the bug. RHEL 8.4 is known to have this kernel version.
Workaround: Downgrading or upgrading the kernel
Downgrading or upgrading the kernel to anything exterior the affected kernel volition resolve the issue
If you still need help, contact support to go your problem resolved apace.
Feedback
Submit and view feedback for
littletonwheme1992.blogspot.com
Source: https://docs.microsoft.com/en-us/azure/storage/files/storage-troubleshooting-files-nfs
0 Response to "Can a Nfs Secuirty Be Used Over Again"
Post a Comment